Learn more about the evolving landscape of zero-day vulnerability management in the wake of Log4Shell.
In 2021, the Log4Shell vulnerability revealed a new magnitude of cyberthreat to the IT world and the limits of zero-day vulnerability management.
Log4Shell was such a sweeping, unwelcome revelation to IT security professionals that many didn’t know how to deal with it. The wake of Log4Shell still reverberates today. DevSecOps teams are still working out ways to prevent a similar threat by improving zero-day vulnerability management. While nobody wants a repeat of Log4Shell, the reality is that more zero-day vulnerabilities have been uncovered “in the wild” over the past 18 months. Organizations must prepare for the worst and have the tools to handle big threats if they do emerge.
At Dynatrace conference Perform 2023, Amit Shah, director of product marketing for application security, and Daniel Kaar, director of application security sales engineering, discussed plans for vigilance and proactivity in the face of potential future threats.
Shah described a game plan for preemptively acting against threats. He noted some of the tools and methods needed to deal with active and emerging attacks or vulnerabilities. Next, Kaar demonstrated real-world examples of how teams can use security dashboards like Dynatrace to prepare for and combat cybersecurity threats.
Security threat response options
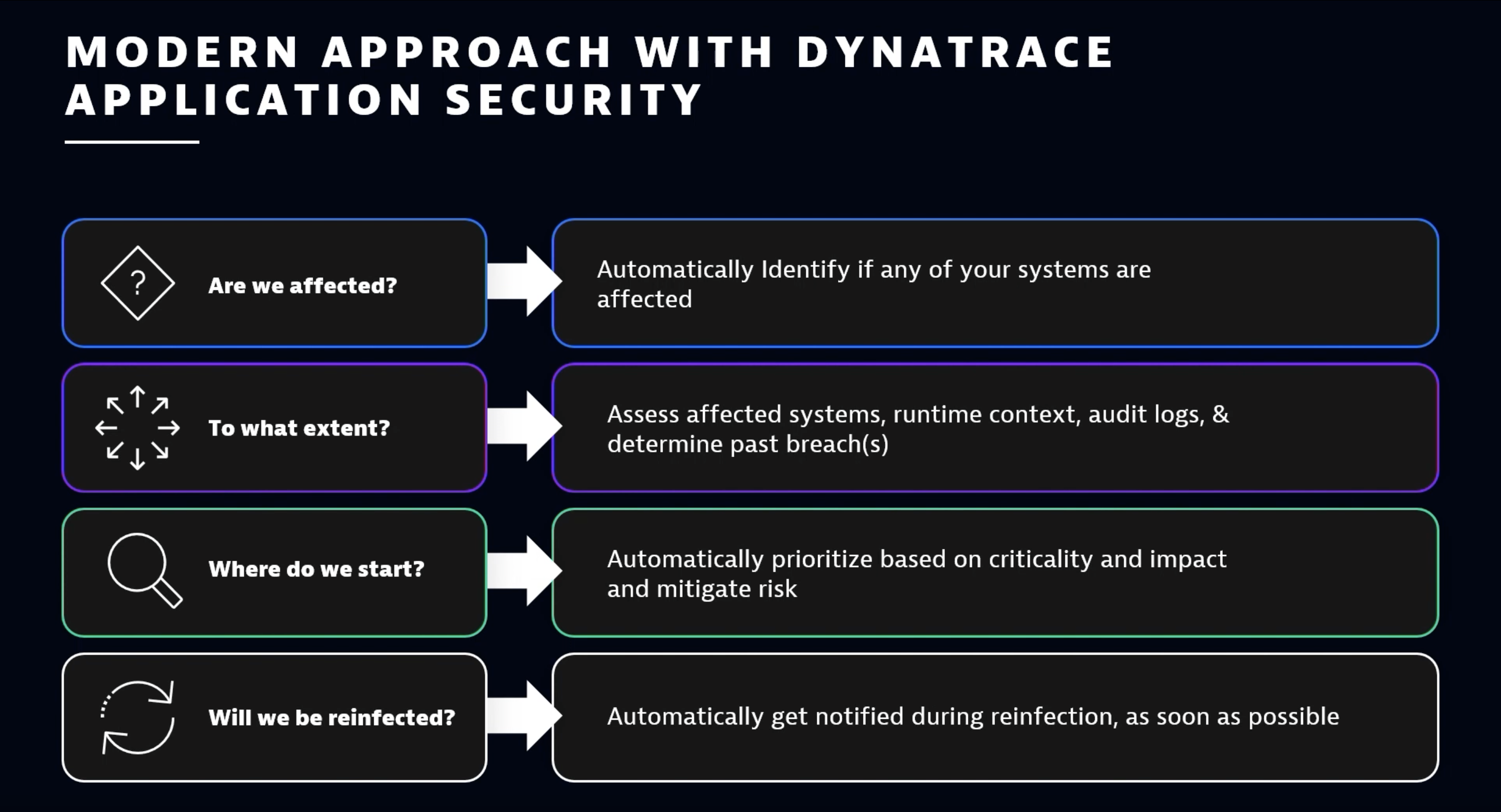
When security teams discover a new vulnerability, Shah posited, they need to answer the following four questions:
- Are we affected?
- To what extent?
- Where do we start?
- Will we be reinfected?
While these questions might merely engage the fundamentals of IT security threat response, how organizations answer them impacts security posture and threat response efficacy. The traditional way of tackling an emerging threat is to address these questions manually. For instance, in response to a threat, SecOps would sift through alerts and logs, identify high-priority alerts, remove false positives and irrelevant alerts, and so on. In the case of a vulnerability, teams would scan the source code to determine whether an organization’s code base is affected and if there’s a chance of reinfection.
However, Shah noted this approach poses serious issues. “Even when that process is followed completely flawlessly, it can take a long time,” said Shah. “One of our customers told us that it took them 92 hours to answer those questions.” Additionally, within that time frame, the organization didn’t determine whether it had already been exploited by the vulnerability. Such manual practices are no longer sufficient for effective zero-day vulnerability management.
These early hours are the most critical after discovering a zero-day vulnerability. If a security team knows about this vulnerability, chances are attackers know as well. Log4Shell was no different, with Microsoft reporting more than 2 million exploitation attempts in the days following the disclosure.
But there are more modern approaches to answering these questions. With Dynatrace Application Security, teams can improve response times and better prepare their organizations for future vulnerabilities.
Modernizing traditional approaches to zero-day vulnerability management with automation
Dynatrace Application Security automatically scans environments for vulnerabilities from a vulnerability database. Once a new exploit or threat enters the database, Dynatrace alerts teams to the issue. AI also assists by ranking different threats, scoring vulnerabilities based on numerous metrics — such as adjacency to the internet and critical data sources — to indicate the urgency of a particular threat. In short, automation both increases response efficacy and frees security teams’ time to address other problems.
Ultimately, Log4Shell has taught security professionals vital lessons about vulnerability response. First, organizations must reduce their security debt. They must assess the solutions and response methods used to handle security threats and update these where necessary. Shah even recommends looking back to Log4Shell and asking, “How long would it take to identify and rectify this now?” Additionally, environment visibility is important for fast detection and response. Automated platforms like Dynatrace can significantly improve security posture, especially in the face of potential code vulnerabilities like Log4Shell.
Vulnerability management and visibility in practice
But what does this modern approach to application security look like? Kaar demonstrated some of Dynatrace’s capabilities and identifies how they can aid teams in dealing with a vulnerability such as Log4Shell.
First, Dynatrace can show a list of all detected vulnerabilities within the environment. Security staff can then view details about each vulnerability, such as its criticality, how many processes it affects, and what the vulnerability does. These are fine-grained views of specific vulnerabilities, but Dynatrace also enables users to view entire components through a security lens. In the component dashboard, teams can customize the layout to show the number of vulnerabilities present in production, how many are high or low priority, and information on vulnerabilities in related services.
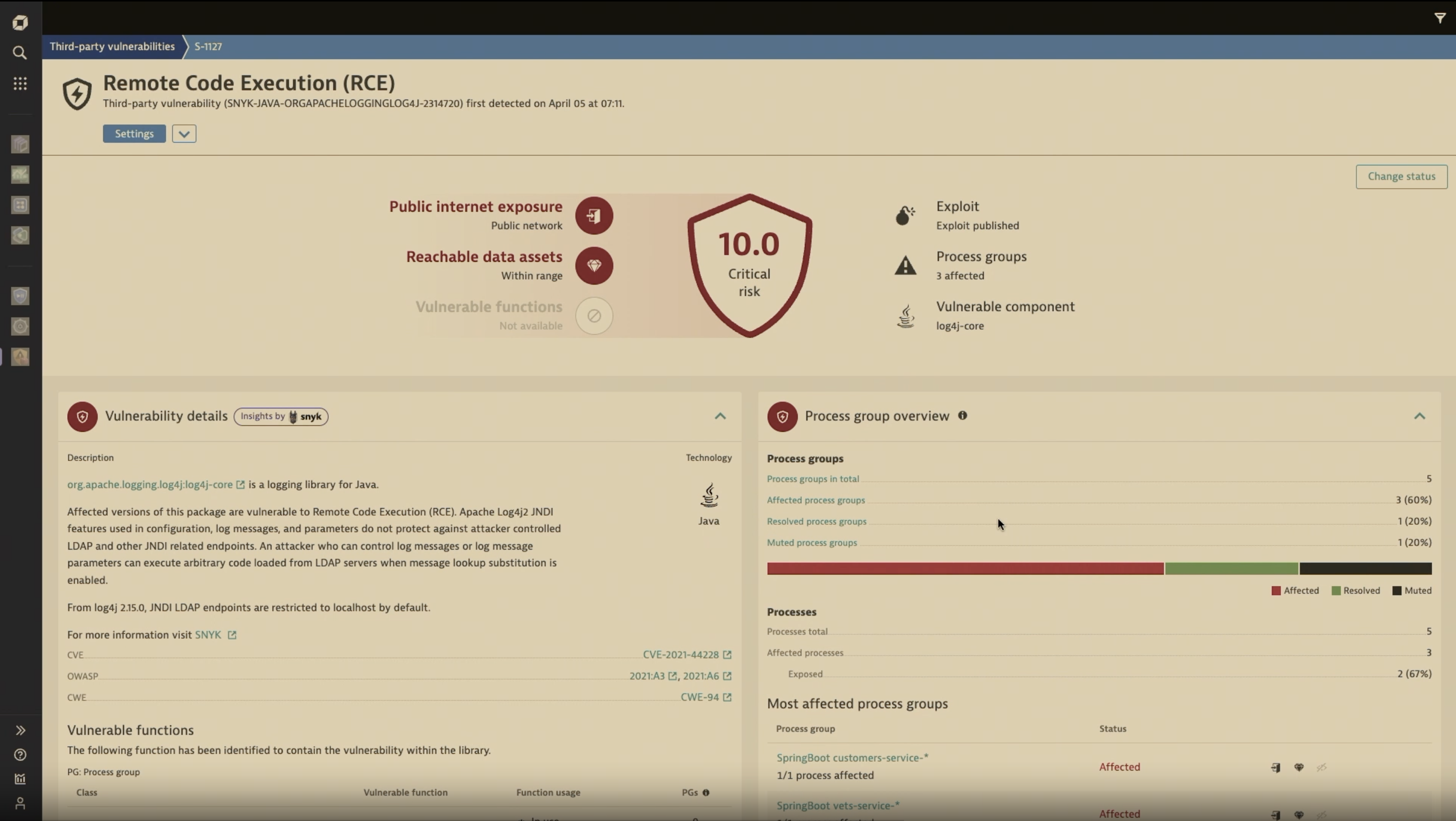
Log4Shell has permanently changed the perspective of IT security. Organizations are evolving their security approaches to meet the new threat landscape. More visibility, more automation, and more AI-powered vulnerability management are key to facing current and future vulnerabilities. These practices also ensure that something like Log4Shell is easy to detect and mitigate, with minimal or no effect on the organization.



Looking for answers?
Start a new discussion or ask for help in our Q&A forum.
Go to forum